开源API网关大全
[TOC]
1. Kong
Kong官网
Kong开源
Openresty + Lua 技术栈
Kong是一个云原生,快速,可扩展和分布式微服务抽象层(也称为API网关,API中间件或在某些情况下为Service Mesh)。 作为2015年的开源项目,其核心价值在于高性能和可扩展性。
Kong积极维护,广泛应用于从创业公司到Global 5000以及政府组织等公司的生产。
Features
- Cloud-Native: Platform agnostic, Kong can run from bare metal to
Kubernetes. - Dynamic Load Balancing: Load balance traffic across multiple upstream
services. - Hash-based Load Balancing: Load balance with consistent hashing/sticky
sessions. - Circuit-Breaker: Intelligent tracking of unhealthy upstream services.
- Health Checks: Active and passive monitoring of your upstream services.
- Service Discovery: Resolve SRV records in third-party DNS resolvers like
Consul. - Serverless: Invoke and secure AWS Lambda or OpenWhisk functions directly
from Kong. - WebSockets: Communicate to your upstream services via WebSockets.
- OAuth2.0: Easily add OAuth2.0 authentication to your APIs.
- Logging: Log requests and responses to your system over HTTP, TCP, UDP,
or to disk. - Security: ACL, Bot detection, whitelist/blacklist IPs, etc…
- Syslog: Logging to System log.
- SSL: Setup a Specific SSL Certificate for an underlying service or API.
- Monitoring: Live monitoring provides key load and performance server
metrics. - Forward Proxy: Make Kong connect to intermediary transparent HTTP proxies.
- Authentications: HMAC, JWT, Basic, and more.
- Rate-limiting: Block and throttle requests based on many variables.
- Transformations: Add, remove, or manipulate HTTP requests and responses.
- Caching: Cache and serve responses at the proxy layer.
- CLI: Control your Kong cluster from the command line.
- REST API: Kong can be operated with its RESTful API for maximum
flexibility. - Geo-Replicated: Configs are always up-to-date across different regions.
- Failure Detection & Recovery: Kong is unaffected if one of your Cassandra
nodes goes down. - Clustering: All Kong nodes auto-join the cluster keeping their config
updated across nodes. - Scalability: Distributed by nature, Kong scales horizontally by simply
adding nodes. - Performance: Kong handles load with ease by scaling and using NGINX at
the core. - Plugins: Extendable architecture for adding functionality to Kong and
APIs.
点评: 开源版本功能基本够用
2. Gravitee
Gravitee官网
Gravitee开源
开发语言:java
Gravitee.io – API Management – OpenSource API Gateway
网关是Gravitee.io平台的核心组件。 您可以将其与“智能”代理进行比较,以了解其目标。
与传统的HTTP代理不同,网关能够根据您的需要将策略(即规则)应用于HTTP请求和响应,这意味着您可以通过添加转换,安全性和许多其他疯狂功能来增强请求和响应处理!
主要功能特性
- REST API:通过 Web UI 执行的每个操作都使用内部的 Rest API
- 一键部署:只需单击一下,API 就会部署到每个 Gravitee.io 网关,并且可以随时使用
- 高可扩展:可以轻松地将新的 Gravitee.io 网关添加到集群中。并且数据已同步,无需浪费时间进行配置
- 自定义策略:Gravitee.io 提供了许多开箱即用的策略(速率限制、CORS、IP过滤等)。如果还不够,可以自己进行开发
- 健康检测:作为 API 提供商,请为你的服务添加运行状况检查,并向你的用户提供有关 API 可用性的反馈


点评: 功能非常全,自带的dashboard也非常好用
3. Zuul
Zuul官网
Zuul开源
开发语言:java
Zuul is a gateway service that provides dynamic routing, monitoring, resiliency, security, and more.
Zuul是一种网关服务,可提供动态路由,监控,弹性,安全性等。
- Authentication and Security – identifying authentication requirements for each resource and rejecting requests that do not satisfy them.
- Insights and Monitoring – tracking meaningful data and statistics at the edge in order to give us an accurate view of production.
- Dynamic Routing – dynamically routing requests to different backend clusters as needed.
- Stress Testing – gradually increasing the traffic to a cluster in order to gauge performance.
- Load Shedding – allocating capacity for each type of request and dropping requests that go over the limit.
- Static Response handling – building some responses directly at the edge instead of forwarding them to an internal cluster
- Multiregion Resiliency – routing requests across AWS regions in order to diversify our ELB usage and move our edge closer to our members
点评: 用Spring Cloud全家桶首选
4. Tky
Tyk官网
Tyk开源
开发语言:golang
Tyk Open Source API Gateway written in Go
Tyk是一个轻量级的开源API网关,管理平台使您能够控制访问API的人员,访问API以及访问API的方式。 Tyk还将记录用户如何与您的API进行交互以及出现问题时的详细分析。
Key Features of Tyk
Tyk offers powerful, yet lightweight features that allow fine grained control over your API ecosystem.
- RESTFul API – Full programmatic access to the internals makes it easy to manage your API users, keys and Api Configuration from within your systems
- Multiple access protocols – Out of the box, Tyk supports Token-based, HMAC Signed, Basic Auth and Keyless access methods
- Rate Limiting – Easily rate limit your API users, rate limiting is granular and can be applied on a per-key basis
- Quotas – Enforce usage quotas on users to manage capacity or charge for tiered access
- Granular Access Control – Grant api access on a version by version basis, grant keys access to multiple API’s or just a single version
- Key Expiry – Control how long keys are valid for
- API Versioning – API Versions can be easily set and deprecated at a specific time and date
- Blacklist/Whitelist/Ignored endpoint access – Enforce strict security models on a version-by-version basis to your access points
- Analytics logging – Record detailed usage data on who is using your API’s (raw data only)
Webhooks – Trigger webhooks against events such as Quota Violations and Authentication failures - IP Whitelisting – Block access to non-trusted IP addresses for more secure interactions
- Zero downtime restarts – Tyk configurations can be altered dynamically and the service restarted without affecting any active request
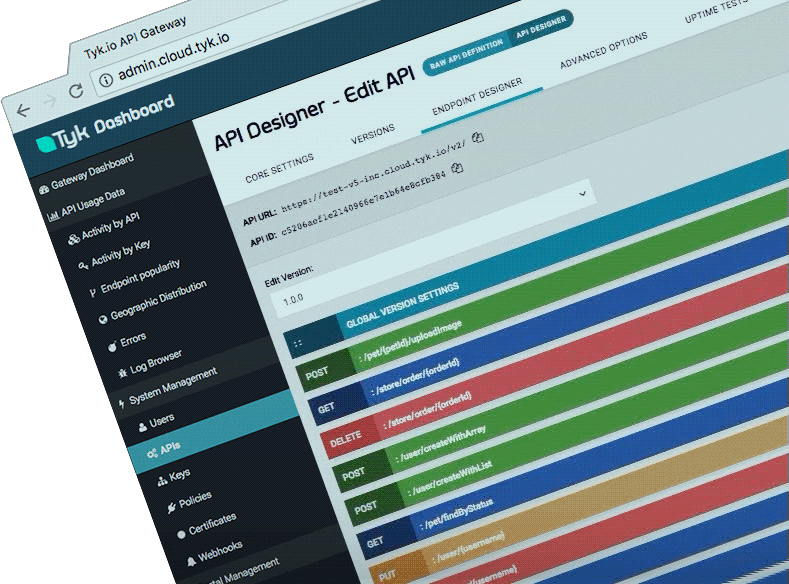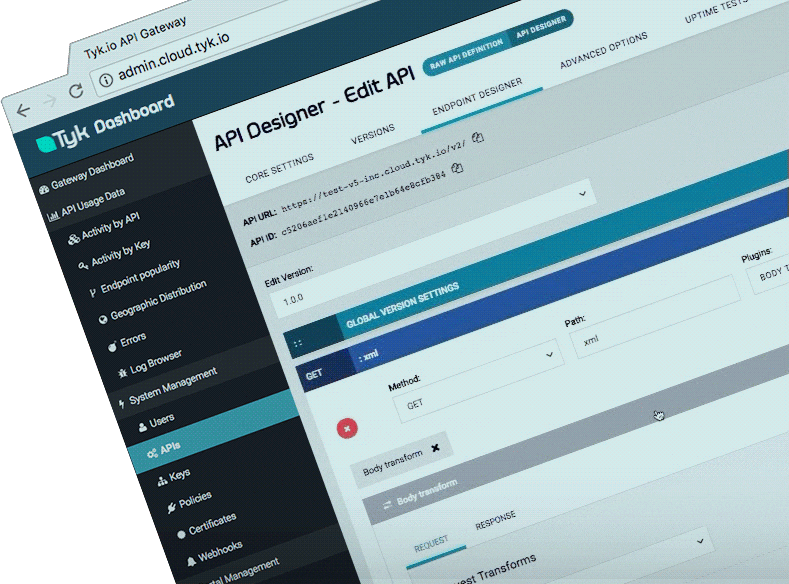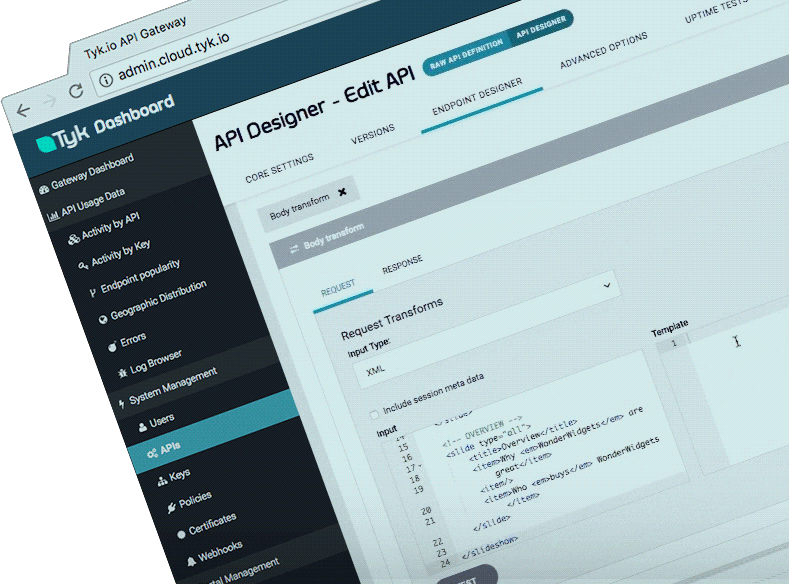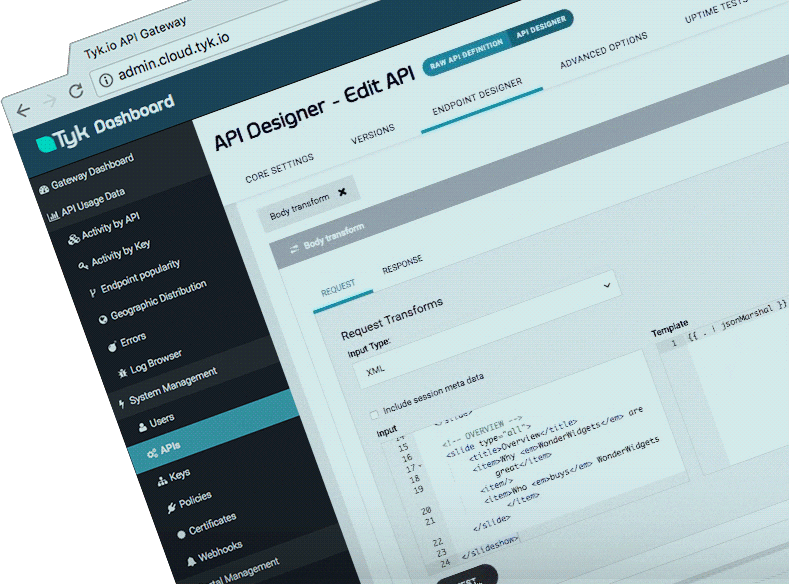
点评: 功能较全,但是授权方面是个问题
5. Manba
GO Gateway网关官网
GO Gateway网关开源
开发语言:golang
Manba是一个基于HTTP协议的restful的API网关。可以作为统一的API接入层。
Features
- 流量控制(Server或API级别)
- 熔断(Server或API级别)
- 负载均衡
- 服务发现
- 插件机制
- 路由(分流,复制流量)
- API 聚合
- API 参数校验
- API 访问控制(黑白名单)
- API 默认返回值
- API 定制返回值
- API 结果Cache
- JWT Authorization
- API Metric导入Prometheus
- API 失败重试
- 后端server的健康检查
- 开放管理API(GRPC、Restful)
- 支持websocket
- 支持在线迁移数据

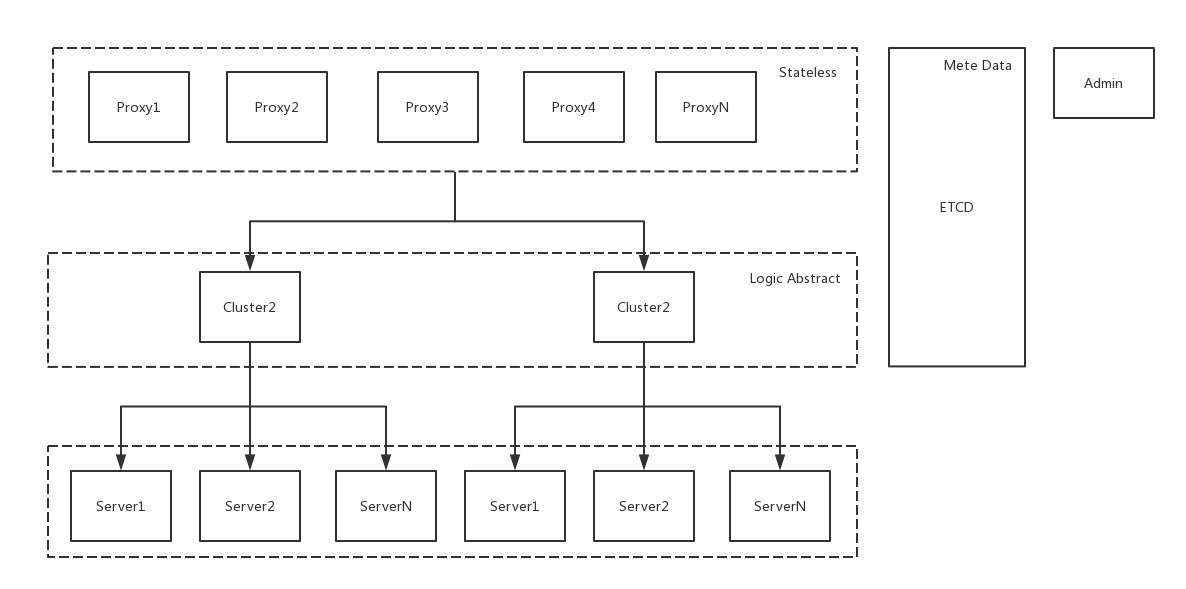
点评: 全开源,自主可控性高
6. GOKU API Gateway
GOKU API Gateway官网
GOKU API Gateway开源
Golang技术栈
GoKu API Gateway CE,中文名:悟空API网关(开源版),是eoLinker旗下的API网关,帮助企业进行API服务治理、API性能安全维护,为企业数字化赋能。
GoKu API Gateway CE,支持OpenAPI与微服务管理,支持私有云部署,实现API转发、请求参数转换、数据校验等功能,提供图形化界面管理,能够快速管理多个API网关,提高API业务安全性。
分ce和ee ce是开源版本,ee是企业版本,企业版本才有插件支持
产品功能
- 管理
访问统计 统计API的访问数据,及时了解API使用情况
图形化界面 通过界面即可设定网关的各项参数
企业人员管理 为企业内部人员分配操作权限
OPEN API 提供完善的OPEN API,方便企业接入内部系统 -
性能与安全
负载均衡 合理分配流量,提高业务的处理能力
权限控制 针对不同用户设定不同的访问权限
集群部署 支持集群部署,提高系统可用性 -
请求转发
支持REST API支持接入REST API
API整合 通过不同的URL访问同一个API
超时重试 超过预设的时间没有得到返回结果,则重新发起请求 -
告警机制
告警邮件 通过邮件接收告警信息
告警推送 通过API接受告警信息 -
拓展
插件支持 提供官方插件,支持自定义插件
导入eoLinker AMS数据支持导入eoLinker AMS的API文档 -
日志系统
请求日志 通过日志详细记录请求过程
告警日志 通过API接受告警信息
插件日志 通过日志详细记录插件使用过程
插件系统
- 用户鉴权
Basic鉴权 通过Basic鉴权访问API
Apikey鉴权 通过Apikey鉴权访问API
OAuth2.0 鉴权通过OAuth2.0鉴权访问API
JWT鉴权 通过JWT鉴权访问API -
流量管控
流量控制 限制单位时间内的最大访问次数
数据缓存 缓存后,用户请求时网关直接返回结果
请求大小限制 在大小限制内的请求才能通过访问 -
安全防御
IP黑白名单 根据IP判断请求合法性
防重放攻击 保证请求的唯一性
跨域插件 设定特定的响应头部实现跨域
返回头部 自定义网关的返回头部 -
参数处理
参数映射 实现参数A转换成参数B
额外参数 转发时可自动添加预设的额外参数
参数校验 通过校验规则的参数方可正常发送
格式转换 参数的json格式与xml格式相互转换 -
响应机制
熔断机制 达到熔断条件网关停止对该API的转发,返回预设内容
服务降级 达到降级条件网关停止对该API的转发,返回降级内容
默认返回 当匹配不到URI时,网关返回预先设定的值

点评:开源版基本不能投产,商业版功能丰富
7. Ocelot
Ocelot官网
Ocelot开源
.NET技术栈
Ocelot是一个.NET API网关。 该项目针对的是使用.NET运行面向微服务/面向服务的体系结构的人,这些体系结构需要统一的入口点。
但是,它可以与任何说HTTP并在ASP.NET Core支持的任何平台上运行的东西一起使用。
Features
- Routing
- Request Aggregation
- Service Discovery with Consul & Eureka
- Service Fabric
- WebSockets
- Authentication
- Authorisation
- Rate Limiting
- Caching
- Retry policies / QoS
- Load Balancing
- Logging / Tracing / Correlation
- Headers / Query String / Claims Transformation
- Custom Middleware / Delegating Handlers
- Configuration / Administration REST API
- Platform / Cloud Agnostic

8. API Umbrella
Open source API management platform
API Umbrella is an open source API management platform for exposing web service APIs.
9. Sentinel
Sentinel官网
Sentinel开源
A lightweight powerful flow control component enabling reliability and monitoring for microservices. (轻量级的流量控制、熔断降级 Java 库)
随着微服务的流行,服务和服务之间的稳定性变得越来越重要。Sentinel 以流量为切入点,从流量控制、熔断降级、系统负载保护等多个维度保护服务的稳定性。
Sentinel 具有以下特征:
丰富的应用场景:Sentinel 承接了阿里巴巴近 10 年的双十一大促流量的核心场景,例如秒杀(即突发流量控制在系统容量可以承受的范围)、消息削峰填谷、集群流量控制、实时熔断下游不可用应用等。
完备的实时监控:Sentinel 同时提供实时的监控功能。您可以在控制台中看到接入应用的单台机器秒级数据,甚至 500 台以下规模的集群的汇总运行情况。
广泛的开源生态:Sentinel 提供开箱即用的与其它开源框架/库的整合模块,例如与 Spring Cloud、Dubbo、gRPC 的整合。您只需要引入相应的依赖并进行简单的配置即可快速地接入 Sentinel。
完善的 SPI 扩展点:Sentinel 提供简单易用、完善的 SPI 扩展接口。您可以通过实现扩展接口来快速地定制逻辑。例如定制规则管理、适配动态数据源等。

10. 3scale
Sentinel官网
Sentinel开源
红帽® 3scale API 管理能让您轻松地管理 API。这个基础架构平台旨在帮助您提升性能、加强客户控制,为未来发展做好准备,通过它,您能快速实现 API 共享、保护、分发、控制和盈利。3scale 可以部署在企业内部、云端或二者的任意组合方案上。
11. Ambassador
Ambassador官网
Ambassador开源
open source Kubernetes-native API gateway for microservices built on the Envoy Proxy
12. APISIX
APISIX官网
APISIX开源
Openresty + Lua 技术栈
APISIX is a cloud-native microservices API gateway, delivering the ultimate performance, security, open source and scalable platform for all your APIs and microservices.
APISIX is based on Nginx and etcd. Compared with traditional API gateways, APISIX has dynamic routing and plug-in hot loading, which is especially suitable for API management under micro-service system.
13. express-gateway
express-gateway官网
express-gateway开源
开发语言:Node.js
Microservices and Serverless to Production Insanely Fast
NODEJS技术栈
14. Gloo
Gloo官网
Gloo开源
An Envoy-Powered API Gateway
15. KrakenD
KrakenD官网
KrakenD开源
An open framework to assemble ultra performance API Gateways with middlewares; core service of the KrakenD API Gateway.
16. Mia-Platform
Mia-Platform官网
Mia-Platform开源
Mia-Platfrom, the API Management platform for enterprises.
17. MuleSoft
MuleSoft官网
MuleSoft开源
Build an application network with secure, reusable integrations and APIs designed, built, and managed on Anypoint Platform™.
18. RIG – Reactive Interaction Gateway
官网
开源
Create low-latency, interactive user experiences for stateless microservices.
19. WSO2 API MICROGATEWAY
官网
开源
API MICROGATEWAY
A cloud-native, developer-centric, decentralized API gateway for microservices.
短评:windows平台
20. Soul
Soul官网
Soul开源
开发语言:java
High-Performance Java API Gateway 高性能微服务API网关
这是一个异步的,高性能的,跨语言的,响应式的API网关。我希望能够有一样东西像灵魂一样,保护您的微服务。参考了Kong,Spring-Cloud-Gateway等优秀的网关后,站在巨人的肩膀上,Soul由此诞生!
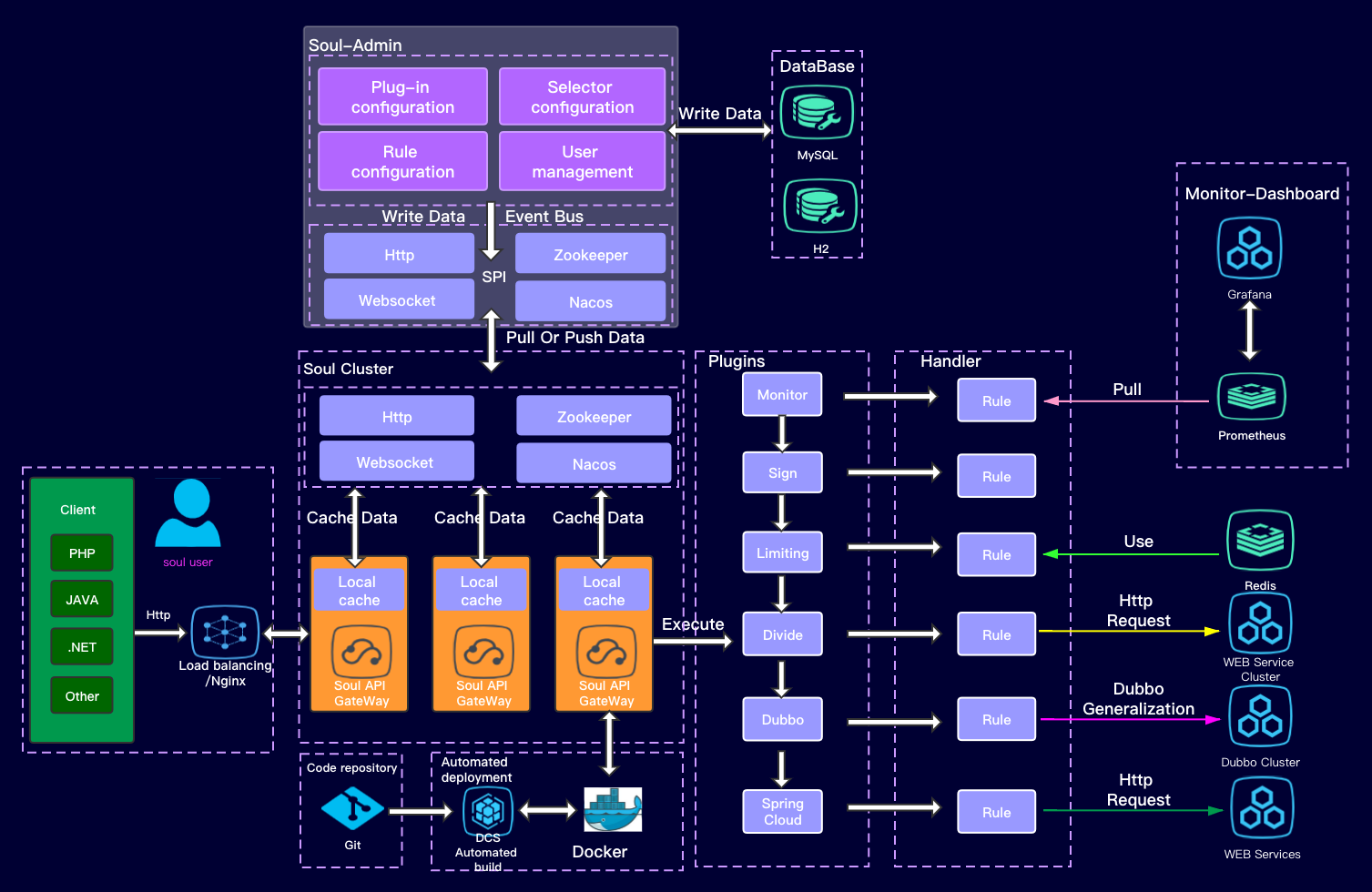
21. BFE
BFE官网
BFE开源
开发语言:golang
百度的前端7层负载均衡器
Open-source layer 7 load balancer derived from proprietary Baidu FrontEnd
BFE is an open-source layer 7 load balancer derived from proprietary Baidu FrontEnd.
22. Fizz Gateway
A Managerment API Gateway in Java . Fizz Gateway 是一个基于 Java开发的微服务网关,能够实现热服务编排、自动授权选择、线上服务脚本编码、在线测试、高性能路由、API审核管理等目的,拥有强大的自定义插件系统可以自行扩展,并且提供友好的图形化配置界面,能够快速帮助企业进行API服务治理、减少中间层胶水代码以及降低编码投入、提高 API 服务的稳定性和安全性。
特性
- 集群管理:Fizz网关节点是无状态的,配置信息自动同步,支持节点水平拓展和多集群部署。
- 服务编排:支持热服务编排能力,支持前后端编码,随时随地更新API。
- 负载均衡:支持round-robin负载均衡。
- 服务发现:支持从Eureka注册中心发现后端服务器。
- 配置中心:支持接入apollo配置中心。
- HTTP反向代理:隐藏真实后端服务,支持 Rest API反向代理。
- 访问策略:支持不同策略访问不同的API、配置不同的鉴权等。
- IP黑白名单:支持配置IP黑白名单。
- 自定义插件:强大的插件机制支持自由扩展。
- 可扩展:简单易用的插件机制方便扩展功能。
- 高性能:性能在众多网关之中表现优异。
- 版本控制:支持操作的发布和多次回滚。
- 管理后台:通过管理后台界面对网关集群进行各项配置。
其他API网关
小豹API网关(收费)
小豹API网关官网
Java技术栈
功能特性介绍
- 认证 支持4种认证方式,包括:Baisc认证、JWT认证、微信小程序Token认证、NULL认证(放行)
- 鉴权 支持2种授权方式,包括:基于接入应用进行授权、NULL授权(放行)
- 流量管控 支持2种流程管理,包括:1、基于客户端应用进行流量管控,防止客户端恶意获取数据。 2、基于API的流量管理,保护上游服务。
- 缓存 缓存API后端服务返回的数据,降低后端服务压力。
- 安全防护 保护API的安全是API网关重任。 1、客户端身份认证;2、只有授权的应用才能访问对应的API。3、公私钥算法保护API接口调用和数据传输安全。4、IP白名单、黑名单机制。5、通过组件二次开发可以扩展很多定制安全功能,如:设备id,地理位置、敏感数据二次检验等。
- 服务路由 识别请求参数和路径转发上游API服务。
- 日志记录 默认以分钟纬度对API调用情况进行汇总记录,也支持配置第三方服务记录完整的API调用详细信息,方便自定义审计和统计。
- 服务注册和暴露 支持Http rest、Webservice服务注册和暴露。
- 负载均衡 支持网关内部负载均衡,用户可以选择注册代理和服务实例地址。
- 服务编排 将多个后端服务聚合成一个API暴露,减小客户端开发复杂度,快速生产新的API。
- 超时控制 通过API配置访问超时时间,超时后立即返回,避免工作线程长时间等等。
- 灰度发布 产品支持让指定部分客户端应用使用新版本API,其他应用继续使用以前的API,当新版本的API逐渐稳定后,所有用户能平滑过渡到新版本的API。使用灰度发布能够及早获得用户的意见反馈,完善产品功能,提升产品质量。让用户参与产品测试,加强与用户互动,降低产品升级所影响的用户范围。
- 熔断 后端服务N秒内连续50%调用出现超时或者异常,系统自动熔断该服务,M秒后尝试恢复链路;该机制可以有效避免无效等等。
- 动态配置更新 运行时变更API、分组、组件等配置,自动同步、及时生效。
- API系统迁移 支持API以系统维度接入API网关,自动纪录API,让API系统迁移自动化。
- 高可用 产品支持企业级高可用部署,避免单点故障。
- 高性能 网关无状态,支持横向扩展,运行时弱依赖持久层,最大化提升网关整体性能。
- 分布式缓存(redis) 当系统API缓存量大时,可使用redis集群提高系统的响应。
- 自定义组件开发 采用组件化的架构,可根据需求通过开发组件匹配企业需求。
- 管理中心 API网关后台管理中心简洁明了,方便API网关管理员对API进行管理,数据面板方便了解系统运行情况。
- 监控中心 监控中心对API运行情况一目了然,通过分析API异常告警辅助系统运维。
- 微信小程序支持 对小程序类型的客户端应用进行了特殊处理,简化小程序对微信用户进行认证,后端服务只需要关系业务逻辑。


您好,你这个文章可以补充上我们的国产API网关么?向您推荐一下。Fizz Gateway,
A Managerment API Gateway in Java . Fizz Gateway 是一个基于 Java开发的微服务网关,能够实现热服务编排、自动授权选择、线上服务脚本编码、在线测试、高性能路由、API审核管理等目的,拥有强大的自定义插件系统可以自行扩展,并且提供友好的图形化配置界面,能够快速帮助企业进行API服务治理、减少中间层胶水代码以及降低编码投入、提高 API 服务的稳定性和安全性。
看了下产品,不错的,已加